Microsoft - MD-102: Endpoint Administrator
Sample Questions
Question: 406
Measured Skill: Manage applications (15–20%)
You have a Microsoft 365 E5 subscription.
The subscription contains users that have devices onboarded to Microsoft Defender for Endpoint. Defender for Endpoint is configured to forward signals to Microsoft Defender for Cloud Apps.
Cloud Discovery identifies a risky web app named App1.
You need to block users from connecting to App1 from Microsoft Edge. Users must be able to bypass the restriction.
Which type of app tag should you use, and what should you configure to integrate Defender for Endpoint with Defender for Cloud Apps?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)
| A | App tag type: Monitored
Integrate by configuring: Asset rule management |
| B | App tag type: Monitored
Integrate by configuring: Enforce app access |
| C | App tag type: Sanctioned
Integrate by configuring: Anonymization |
| D | App tag type: Sanctioned
Integrate by configuring: Asset rule management |
| E | App tag type: Unsanctioned
Integrate by configuring: Anonymization |
| F | App tag type: Unsanctioned
Integrate by configuring: Enforce app access |
Correct answer: FExplanation:
The Microsoft Defender for Cloud Apps integration with Microsoft Defender for Endpoint provides a seamless Shadow IT visibility and control solution. Our integration enables Defender for Cloud Apps administrators to block access of end users to cloud apps, by natively integrating Defender for Cloud Apps app governance controls with Microsoft Defender for Endpoint's network protection. Alternatively, administrators can take a gentler approach of warning users when they access risky cloud apps.
Defender for Cloud Apps uses the built-in Unsanctioned app tag to mark cloud apps as prohibited for use, available in both the Cloud Discovery and Cloud App Catalog pages. By enabling the integration with Defender for Endpoint, you can seamlessly block access to unsanctioned apps with a single click in Defender for Cloud Apps.
Apps marked as Unsanctioned in Defender for Cloud Apps are automatically synced to Defender for Endpoint. More specifically, the domains used by these unsanctioned apps are propagated to endpoint devices to be blocked by Microsoft Defender Antivirus within the Network Protection SLA.
Admins have the option to warn users when they access risky apps. Rather than blocking users, they're prompted with a message providing a custom redirect link to a company page listing apps approved for use. The prompt provides options for users to bypass the warning and continue to the app. Admins are also able to monitor the number of users that bypass the warning message.
Use the following steps to enable access control for cloud apps:
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Cloud Discovery, select Microsoft Defender for Endpoint, and then select Enforce app access.
Reference: Govern discovered apps using Microsoft Defender for Endpoint
Question: 407
Measured Skill: Manage and maintain devices (30–35%)
You have a Microsoft 365 E5 subscription that contains Windows 11 devices.
All the devices are onboarded to Microsoft Defender for Endpoint.
You need to compare the configuration of the devices against industry standard benchmarks.
What should you use?| A | Attack surface map |
| B | Events |
| C | Security baselines assessment |
| D | Initiatives |
Correct answer: CExplanation:
Security baselines are standardized documents for Azure product offerings, describing the available security capabilities and the optimal security configurations to help you strengthen security through improved tooling, tracking, and security features.
Security baselines for Azure focus on cloud-centric control areas in Azure environments. These controls are consistent with well-known industry standards such as: Center for Internet Security (CIS) or National Institute for Standards in Technology (NIST).
Each baseline consists of the following components:
- How does a service behave?
- Which security features are available?
- What configurations are recommended to secure the service?
References:
Security baselines for Azure
Security baselines assessment
Question: 408
Measured Skill: Manage applications (15–20%)
You have a Microsoft 365 E5 subscription.
You plan to create a Conditional Access policy named Policy1.
You need to ensure that only Passwordless MFA authentication methods are used when administrators attempt to access the Azure portal, Azure PowerShell, or Azure Command-Line Interface (CLI).
How should you configure Policy1?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)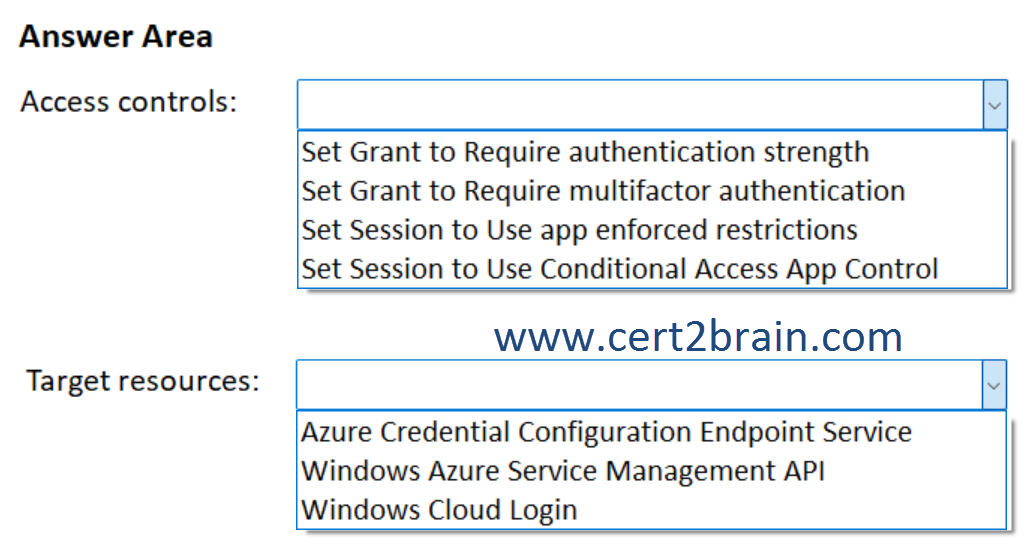
| A | Access controls: Set Grant to Require authentication strength
Target resources: Azure Credential Configuration Endpoint Service |
| B | Access controls: Set Session to Use app enforced restrictions
Target resources: Azure Credential Configuration Endpoint Service |
| C | Access controls: Set Session to Use Conditional Access App Control
Target resources: Windows Azure Service Management API |
| D | Access controls: Set Grant to Require authentication strength
Target resources: Windows Azure Service Management API |
| E | Access controls: Set Grant to Require multifactor authentication
Target resources: Windows Cloud Login |
| F | Access controls: Set Session to Use app enforced restrictions
Target resources: Windows Cloud Login |
Correct answer: DExplanation:
Authentication strength is a Conditional Access control that specifies which combinations of authentication methods can be used to access a resource. Users can satisfy the strength requirements by authenticating with any of the allowed combinations.
For example, an authentication strength can require that only phishing-resistant authentication methods be used to access a sensitive resource. To access a nonsensitive resource, administrators can create another authentication strength that allows less secure multifactor authentication (MFA) combinations, such as password + text message.
The Passwordless MFA strength includes authentication methods that satisfy MFA but don't require a password.
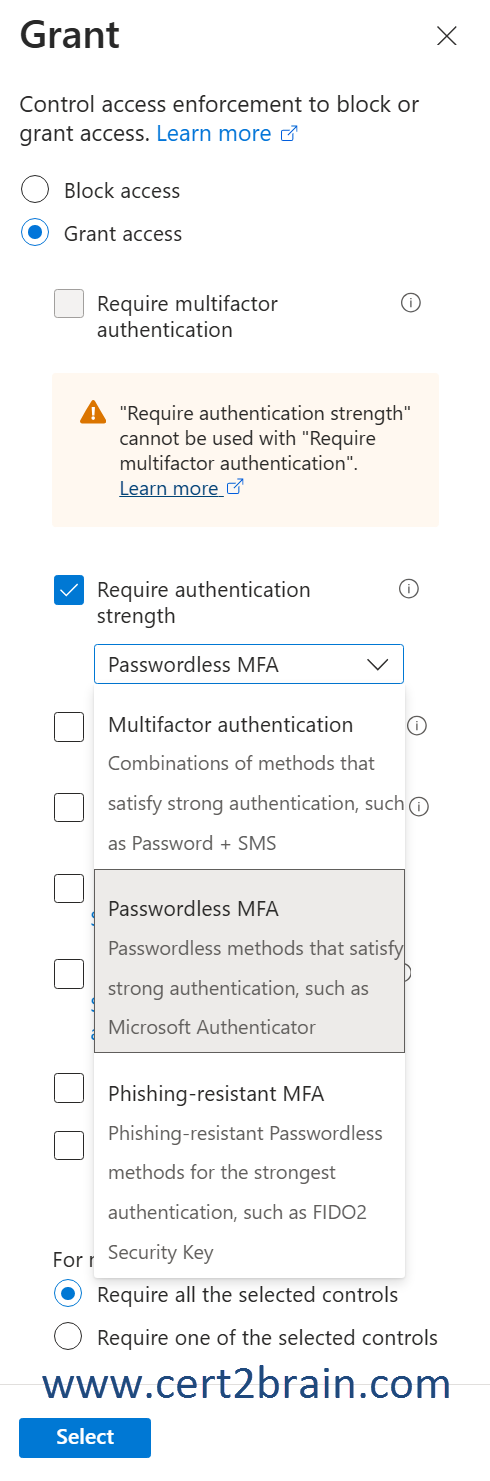
Windows Azure Service Management API
When you target the Windows Azure Service Management API application, policy is enforced for tokens issued to a set of services closely bound to the portal. This grouping includes the application IDs of:
- Azure Resource Manager
- Azure portal, which also covers the Microsoft Entra admin center
- Azure Data Lake
- Application Insights API
- Log Analytics API
Because the policy is applied to the Azure management portal and API, any services or clients that depend on the Azure API can be indirectly affected. For example:
- Azure CLI
- Azure Data Factory portal
- Azure DevOps
- Azure Event Hubs
- Azure PowerShell
- Azure Service Bus
- Azure SQL Database
- Azure Synapse
- Classic deployment model APIs
- Microsoft 365 admin center
- Microsoft IoT Central
- SQL Managed Instance
- Visual Studio subscriptions administrator portal
References:
Conditional Access authentication strength
Conditional Access: Target resources
Question: 409
Measured Skill: Manage and maintain devices (30–35%)
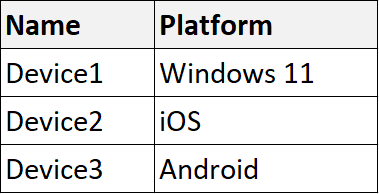
You have a Microsoft 365 E5 subscription that contains devices enrolled in Microsoft Intune as shown in the following table.
The subscription contains the users shown in the following table.
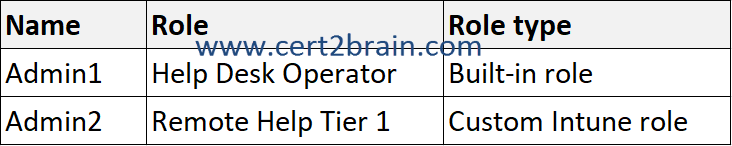
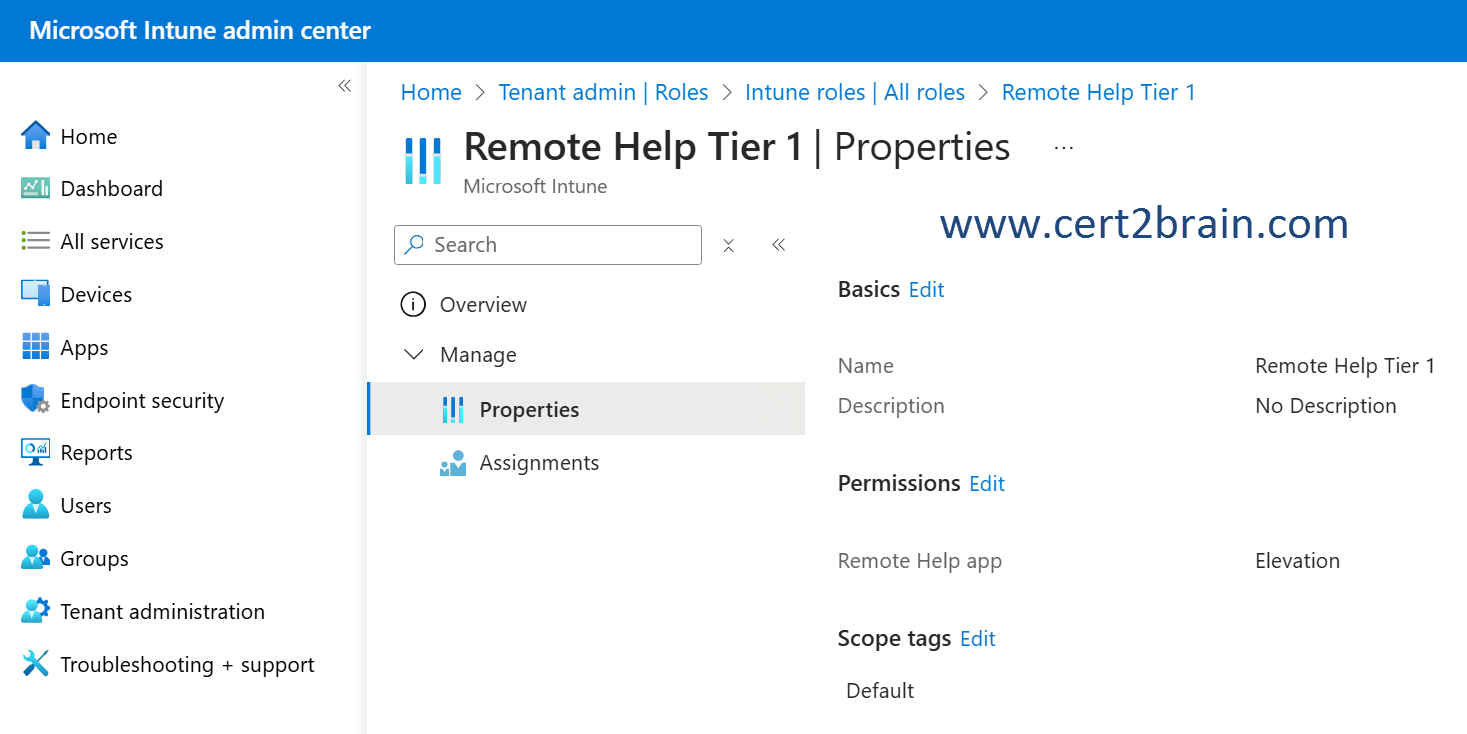
The Remote Help Tier 1 role is configured as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
(NOTE: Each correct selection is worth one point.)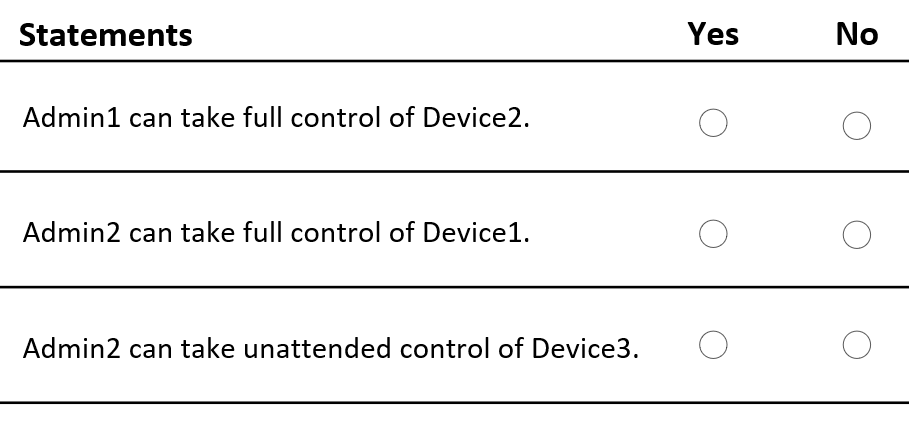
| A | Admin1 can take full control of Device2: Yes
Admin2 can take full control of Device1: Yes
Admin2 can take unattended control of Device3: Yes |
| B | Admin1 can take full control of Device2: Yes
Admin2 can take full control of Device1: Yes
Admin2 can take unattended control of Device3: No |
| C | Admin1 can take full control of Device2: Yes
Admin2 can take full control of Device1: No
Admin2 can take unattended control of Device3: No |
| D | Admin1 can take full control of Device2: No
Admin2 can take full control of Device1: Yes
Admin2 can take unattended control of Device3: Yes |
| E | Admin1 can take full control of Device2: No
Admin2 can take full control of Device1: No
Admin2 can take unattended control of Device3: Yes |
| F | Admin1 can take full control of Device2: No
Admin2 can take full control of Device1: No
Admin2 can take unattended control of Device3: No |
Correct answer: CExplanation:
Admin1 has the Help Desk Operator role assigned. The role grants all four Remote Help app permissions, which include:
- Elevation
- View screen
- Unattended control
- Take full control
Admin2 has the Remote Help Tier 1 role assigned. The role does not grant the Take full control Remote Help app permisson. Admin2 can't take full control of Device1.
Admin2 has the Remote Help Tier 1 role assigned. The role does not grant the Unattended control Remote Help app permisson. Admin2 can't take unattended control of Device3.
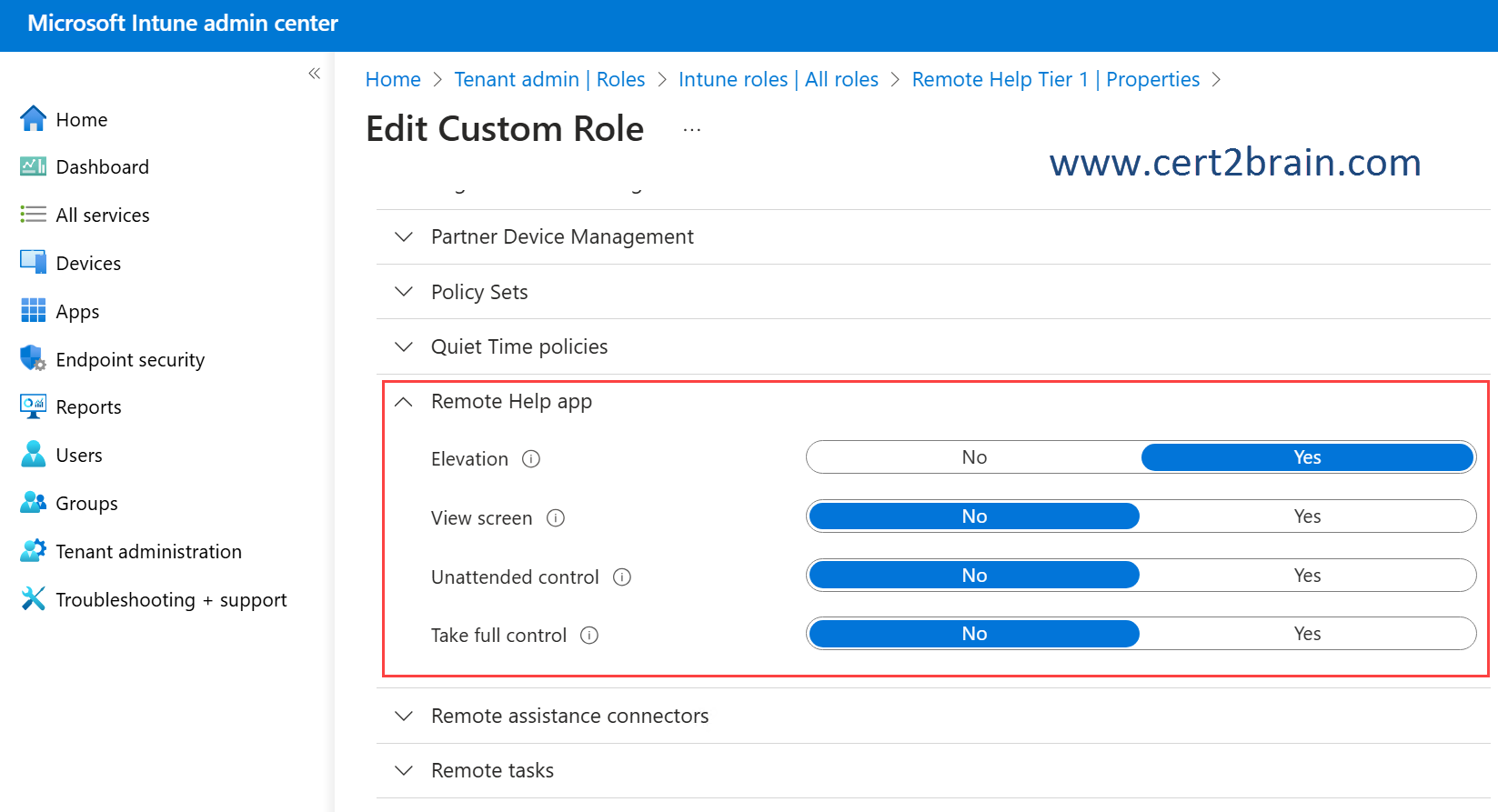
Remote Help app - Elevation
For Windows devices, elevation allows the helper to enter UAC credentials when prompted on the sharer’s device when remote help is enabled. Enabling elevation also allows the helper to view and control the sharer’s device when the sharer grants the helper access.
Question: 410
Measured Skill: Manage applications (15–20%)
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Cloud Apps.
You plan to perform a security audit of all the apps detected by Cloud Discovery.
You need to track which apps were audited. The solution must ensure that the list of audited apps can be displayed in the cloud app catalog.
What should you do?| A | Apply a custom app tag to each app. |
| B | Deploy Conditional Access App Control. |
| C | Define each app as a critical asset. |
| D | Generate a Cloud Discovery snapshot report. |
| E | Enable app governance. |
Correct answer: AExplanation:
When you have a large number of discovered apps, you'll find it useful to filter and query them.
In Microsoft Defender for Cloud Apps you can create custom app tags. These tags can then be used as filters for deeper diving into specific types of apps that you want to investigate. For example, custom watch list, assignment to a specific business unit, or custom approvals, such as "approved by legal". App tags can be also used in app discovery policies in filters or by applying tags to apps as part of the policy governance actions.
Reference: Filter and query discovered apps in Microsoft Defender for Cloud Apps