Microsoft - MS-102: Microsoft 365 Administrator
Sample Questions
Question: 415
Measured Skill: Implement and manage Microsoft Entra identity and access (25-30%)
You have a Microsoft 365 E5 subscription.
You need to create a Conditional Access policy named Policy1 that meets the following requirements:
- Applies to high-risk users
- Requires multifactor authentication (MFA)
Which two settings should you configure?
(To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.)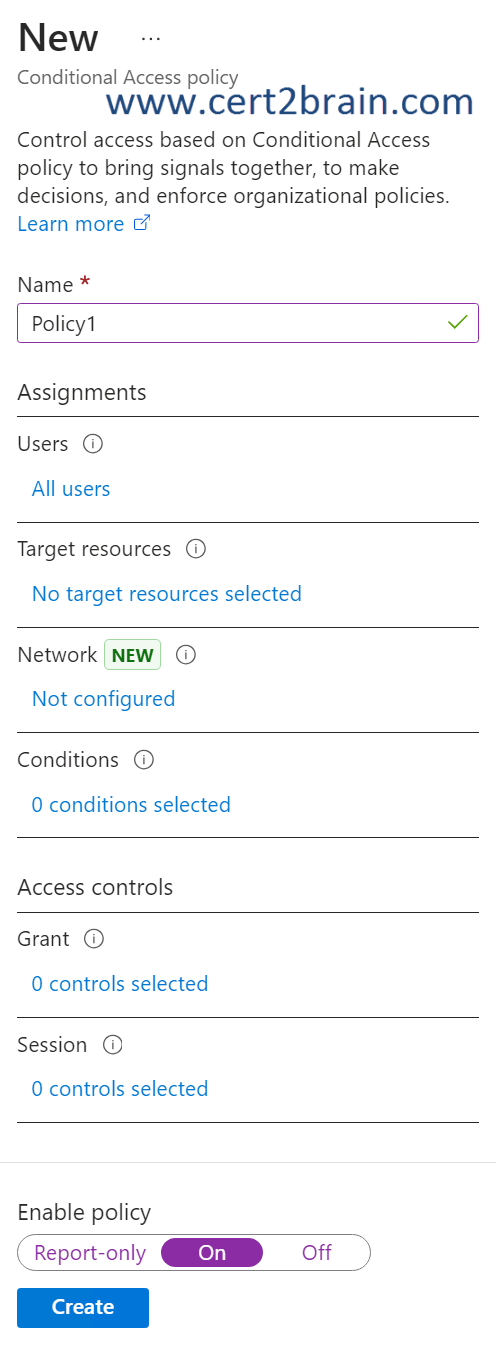
| A | Assignments - Users |
| B | Assignments - Target resources |
| C | Assignments - Network |
| D | Assignments - Conditions |
| E | Access Controls - Grant |
| F | Access Controls - Session |
Correct answer: D, EExplanation:
We need to configure the User risk condition as shown below.
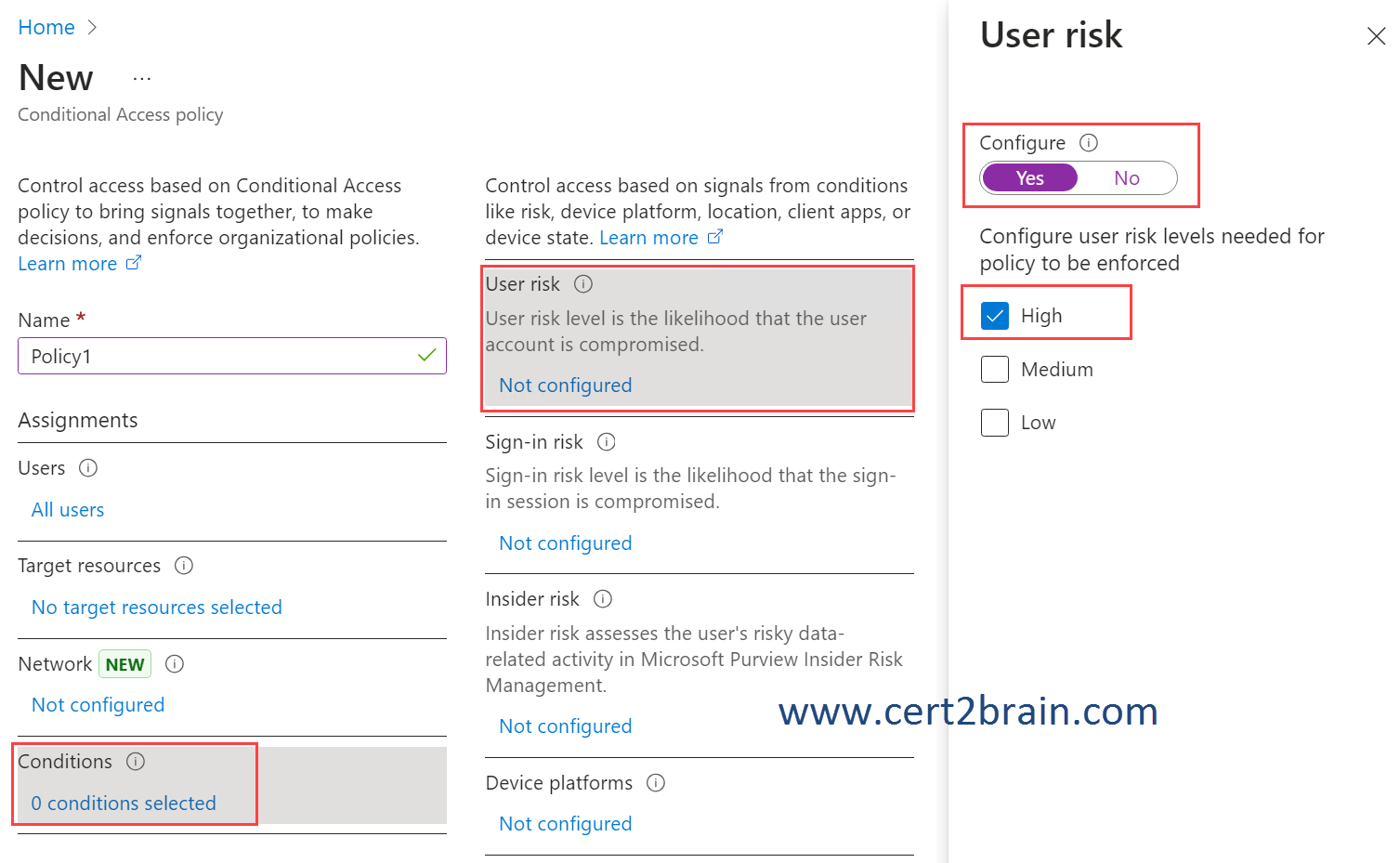
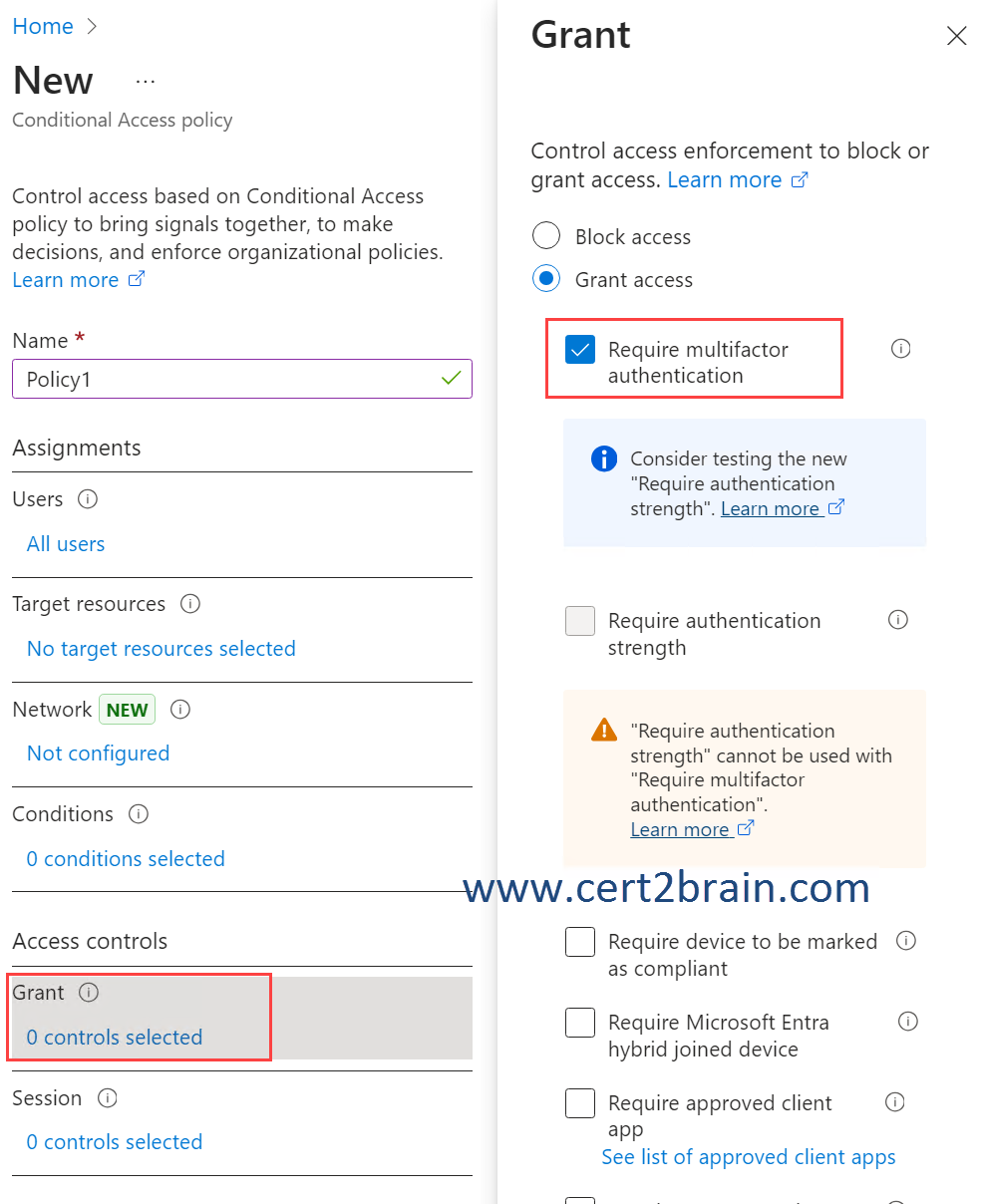
And require multifactor authentication from the Grant control.
Question: 416
Measured Skill: Deploy and manage a Microsoft 365 tenant (10-15%)
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Endpoint. The subscription contains the devices shown in the following table.
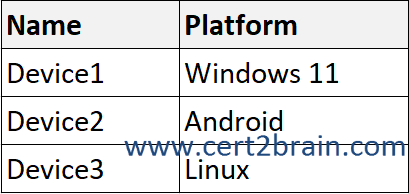
You need to create the Endpoint security policies shown in the following table.
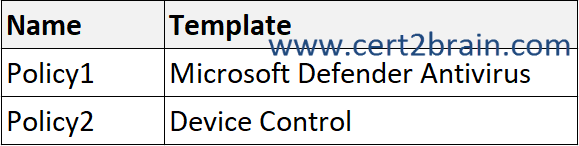
To which device can you apply each policy?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)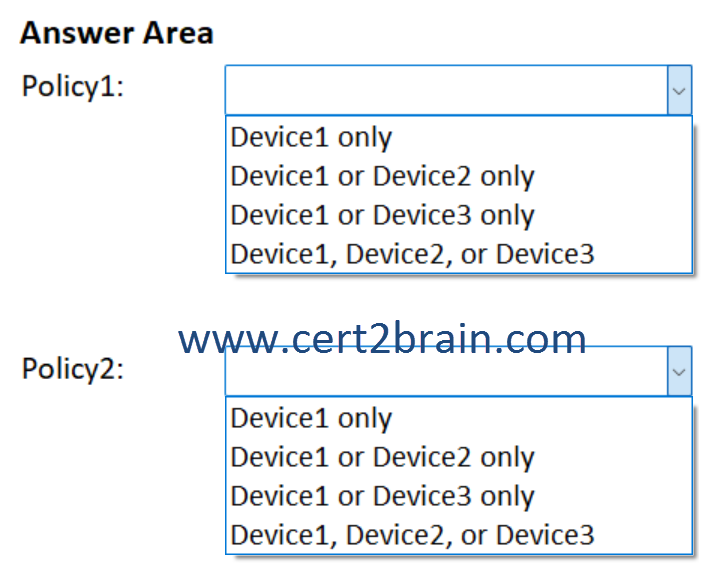
| A | Policy1: Device1 only
Policy2: Device1, Device2, or Device3 |
| B | Policy1: Device1 only
Policy2: Device1 or Device3 only |
| C | Policy1: Device1 or Device2 only
Policy2: Device1 only |
| D | Policy1: Device1 or Device2 only
Policy2: Device1, Device2, or Device3 |
| E | Policy1: Device1 or Device3 only
Policy2: Device1 only |
| F | Policy1: Device1, Device2, or Device3
Policy2: Device1 or Device2 only |
Correct answer: EExplanation:
As a security admin concerned with device security, use Intune endpoint security policies to manage security settings on devices. These profiles are similar in concept to a device configuration policy template or security baseline, which are logical groups of related settings. However where device configuration profiles and security baselines include a large body of diverse settings outside the scope of securing endpoints, each endpoint security profile focuses on a specific subset of device security.
The Microsoft Defender Antivirus Endpoint security policy template is available for Windows, macOS, and Linux devices.
The Device Control Endpoint security policy template is available for Windows only.
References:
Manage device security with endpoint security policies in Microsoft Intune
Antivirus policy for endpoint security in Intune
Deploy and manage device control in Microsoft Defender for Endpoint with Microsoft Intune
Question: 417
Measured Skill: Manage security and threats by using Microsoft Defender XDR (35–40%)
You use Microsoft Defender for Office 365.
You plan to automate an attack simulation campaign.
Any users that fail the simulation must take additional training based on the simulation results.
What is the maximum number of days the training will be available to the users after the simulation?Correct answer: CExplanation:
In Attack simulation training in Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2, simulations are benign cyberattacks that you run in your organization. These simulations test your security policies and practices, as well as train your employees to increase their awareness and decrease their susceptibility to attacks.
On the Assign training page, you can assign trainings for the simulation. We recommend that you assign training for each simulation, as employees who go through training are less susceptible to similar attacks.
In Select a training due date, you can choose one of the following values:
- 30 days after simulation ends (this is the default value)
- 15 days after simulation ends
- 7 days after simulation ends
Reference: Simulate a phishing attack with Attack simulation training
Question: 418
Measured Skill: Manage security and threats by using Microsoft Defender XDR (35–40%)
You have a Microsoft 365 E5 subscription.
The subscription contains users that have devices onboarded to Microsoft Defender for Endpoint. Defender for Endpoint is configured to forward signals to Microsoft Defender for Cloud Apps.
Cloud Discovery identifies a risky web app named App1.
You need to block users from connecting to App1 from Microsoft Edge. Users must be able to bypass the restriction.
Which type of app tag should you use. and what should you configure to integrate Defender for Endpoint with Defender for Cloud Apps?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)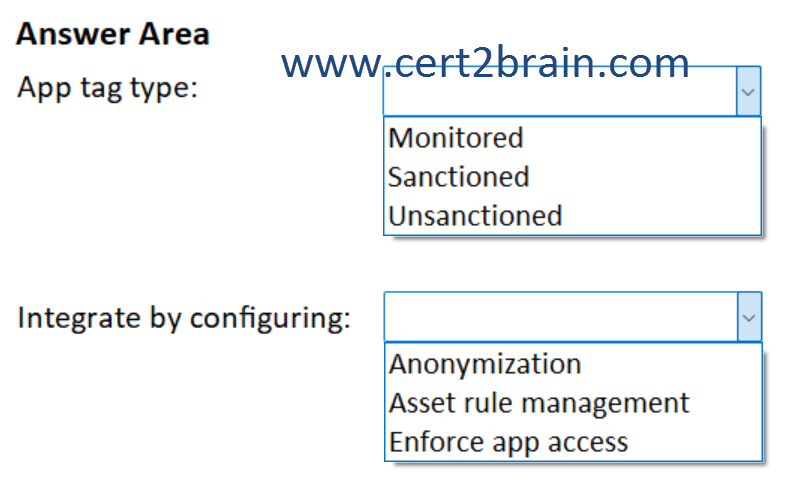
| A | App tag type: Monitored
Integrate by configuring: Anonymization |
| B | App tag type: Monitored
Integrate by configuring: Enforce app access |
| C | App tag type: Sanctioned
Integrate by configuring: Anonymization |
| D | App tag type: Sanctioned
Integrate by configuring: Asset rule management |
| E | App tag type: Unsanctioned
Integrate by configuring: Enforce app access |
| F | App tag type: Unsanctioned
Integrate by configuring: Asset rule management |
Correct answer: BExplanation:
Admins have the option to warn users when they access risky apps. Rather than blocking users, they're prompted with a message providing a custom redirect link to a company page listing apps approved for use. The prompt provides options for users to bypass the warning and continue to the app. Admins are also able to monitor the number of users that bypass the warning message.
Defender for Cloud Apps uses the built-in Monitored app tag to mark cloud apps as risky for use. The tag is available on both the Cloud Discovery and Cloud App Catalog pages. By enabling the integration with Defender for Endpoint, you can seamlessly warn users on access to monitored apps with a single click in the Defender for Cloud Apps portal.
To enable cloud app blocking with Defender for Endpoint you need to enable Enforce app access from the Cloud Apps setting in the Microsoft Defender Portal.
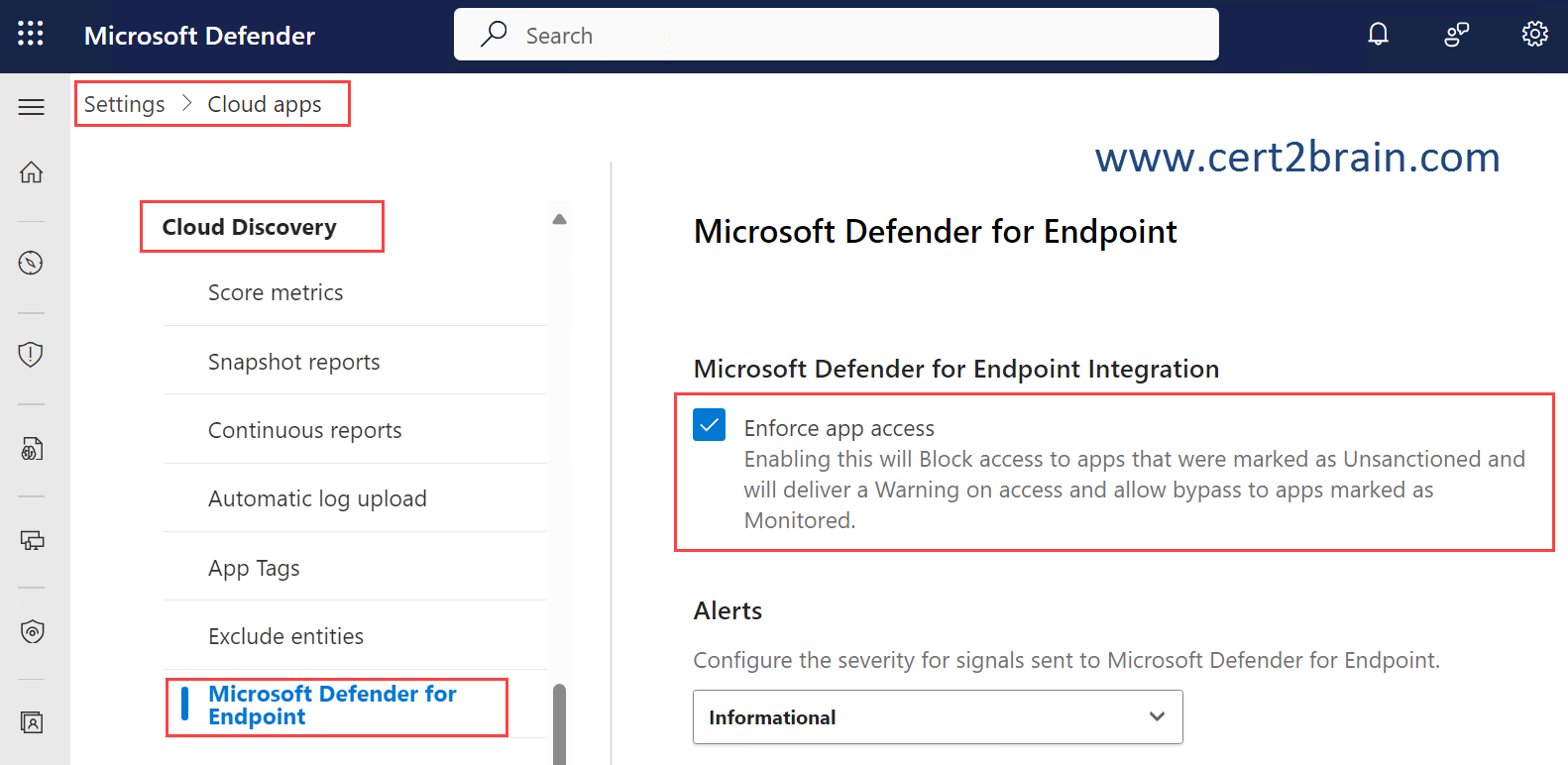
References:
Govern discovered apps
Govern discovered apps using Microsoft Defender for Endpoint
Question: 419
Measured Skill: Implement and manage Microsoft Entra identity and access (25-30%)
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.
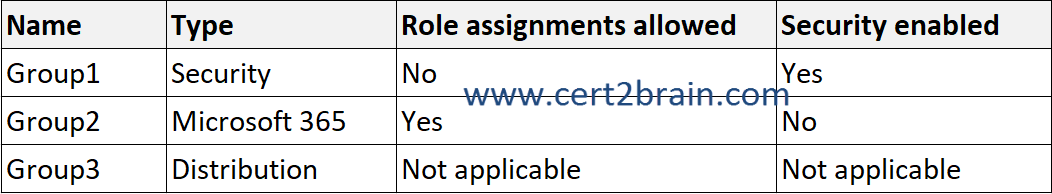
You plan to create 10 new users and configure group-based licensing to assign each user a Microsoft 365 E5 license.
To which group should you add the users, and which portal should you use to assign the license?
(To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.)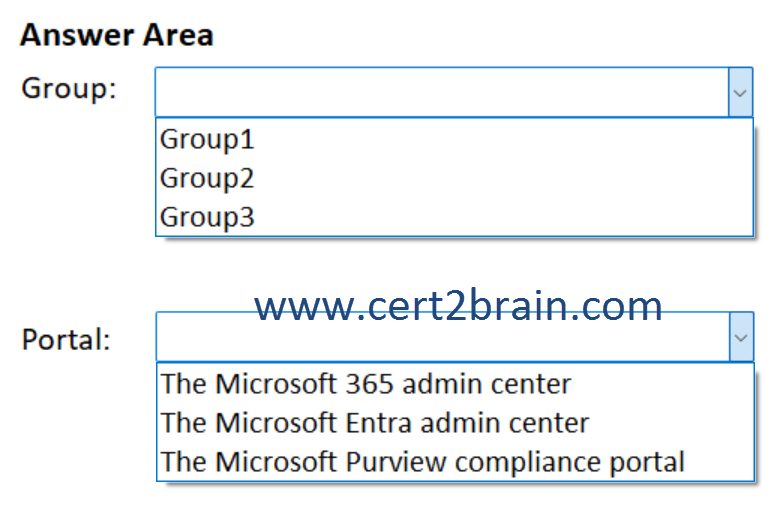
| A | Group: Group1
Portal: The Microsoft Entra admin center |
| B | Group: Group1
Portal: The Microsoft 365 admin center |
| C | Group: Group2
Portal: The Microsoft Purview compliance portal |
| D | Group: Group2
Portal: The Microsoft 365 admin center |
| E | Group: Group3
Portal: The Microsoft Entra admin center |
| F | Group: Group3
Portal: The Microsoft Purview compliance portal |
Correct answer: BExplanation:
Licenses can be assigned to any security group in Microsoft Entra ID. Security groups can be synced from on-premises, by using Microsoft Entra Connect. You can also create security groups directly in Microsoft Entra ID (also called cloud-only groups), or automatically via the Microsoft Entra dynamic group feature.
Starting September 1st 2024, the Microsoft Entra ID Admin Center and the Microsoft Azure portal will no longer support license assignment through their user interfaces. To manage license assignments for users and groups, administrators must use the Microsoft 365 Admin Center. This update is designed to streamline the license management process within the Microsoft ecosystem. This change is limited to the user interface. API and PowerShell access remain unaffected.
References:
What is group-based licensing in Microsoft Entra ID?
Assign licenses to users by group membership in Microsoft Entra ID